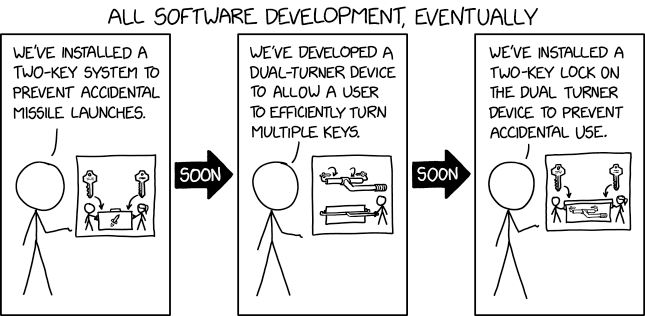
Two Key System
Our company can be your one-stop shop for decentralization.

Our company can be your one-stop shop for decentralization.
As an allegory, the comic relates the results of software development to the reputed safeguards of nuclear missile launch systems. Such precautions include the need for two independent operators for authorization, to prevent honest mistakes or the rogue actions of lone-actors. This is the kind of procedure used at a launch site where two duty officers each need to turn their respective keys simultaneously. The physical distance between the keys ensures that an individual cannot turn both keys simultaneously, or initiate the sequence without the second person.
In relation to software development, the inconvenience caused by such precautions (like account passwords and two-factor authentication) has prompted the development of methods to make the process easier (like autofilling passwords or website cookies keeping a user logged in for multiple visits). Similarly, the system in the comic is made more convenient by using a dual key-turner that circumvents the need for two users to turn the keys.
And thus we find out that the thing used to make the safeguards less of a nuisance actually defeats the purpose of the safeguards. As with website passwords, where the use of a computer or device by someone else could allow them to use the autologin capabilities, or even to view all passwords used locally and take away for their own use, the whole point of the deliberately included security factor has been negated. It was only the perceived need for two independent operators that created the initial situation of requiring two separated keys, or indeed any keys at all!
Hence, after a further cycle of development, in order to restore the security of the two-key system, the two-key turning device (rather than being removed or made unworkable) is provided for use but only if it can be removed from a secure cabinet (labelled as giving access to the 'key turner', much as the original unit was labelled as giving access to a missile) with the requirements to open it being… two separate keys to be used at the same time! This could be seen as the same as password managers being introduced, either as a part of a browser or third-party add-ons, which automatically provide the user's passwords for any given access attempt but only when they are given a password (or other security factor) themselves. Rather than removing a 'problem', a new safeguard is added which does the exact same thing as the original, the possible nuisance (but hopefully also the necessary element of security) included.
Password management, as a process, is substantially similar to key management: Common failure-modes for both passwords and keys, include forgetting your own long-term passwords (especially if you changed computers after asking your computer to remember your passwords for you) which is functionally similar to misplacing your keys, or tending to use just a single password or key for every lock (which, if ever compromised in one situation, may lead to being compromised across many others). A Password Manager can reduce such issues, as it can be capable of 'spitting out' or transfering login details at will and letting you use many different passwords (even generating and using the kinds of passwords nobody should be able to guess, or remember!) across your many different websites, etc. But this passkey storage must itself be secure, and so should be functionally accessible perhaps only through use of a 'master passkey' or some other kind of authentication process, which may be subject to the same issues of forgetting, copying, or theft. Similarly, a central lockbox full of keys (such as those used at some car dealerships), can make handling multiple keys much easier, while introducing a single point of failure in the event that lockbox is illicitly accessed. Various forms of multi-factor authentication, plus auxiliary authentication methods for password recovery/reset, go some way to alleviate these challenges, at the expense of further intermediary steps and hardware requirements; but the balance between ease of use and security is never quite so simple and universal.
The title text mentions a one-stop-shop for decentralization. The drive to make use of "one-stop-shops" (such as a website aggregating searches for the best insurance) and also to decentralize (in this case not relying upon any one vendor, even that single aggregator who might actually not be the best aggregator) is another self-contradiction — because a one-stop-shop is by definition centralized.
The comic being posted on September 26th may or may not be a reference to Stanislav Petrov correctly rejecting the false detection of an incoming nuclear missile strike from the US on September 26th, 1983. When asked whether or not this reference was intentional, Randall has continuously declined to comment. 2052: Stanislav Petrov Day
For a related xkcd on security and software cycles, see 2044: Sandboxing Cycle.